High Security,
Low Hassle
Ensure security posture and accelerate
compliance for any embedded device
Karamba's end-to-end portfolio enables OEMs, suppliers, and embedded device manufacturers to secure their products and comply with industry regulations, without interfering with their R&D activities or delaying product release schedules.
Trusted by
Featured Case Studies

Secure Trucks’ Telematics/Gateway
Seamless hardening of trucks, enabling retrofitting a fleet of 1M trucks

Meet FDA Regulations
Enabling a medical device manufacturer to meet customer and regulatory premarket requirements

Solar Inverter Security
Secure existing inverter architecture, deployed in over 128 countries
Karamba’s End-to-End Product Security
Discover.Mitigate.Comply.
Discover.
Product Vulnerabilities before Start of Production
TARA
During the threat analysis risk assessment (TARA) process, Karamba uncovers design and architectural risks vulnerabilities in the IoT product. Karamba prioritizes those gaps and offers ways to mitigate them.
Penetration Testing
Karamba’s penetration testing services enable OEMs, suppliers and device manufacturers to uncover critical cyber vulnerabilities, and address them before start of production.
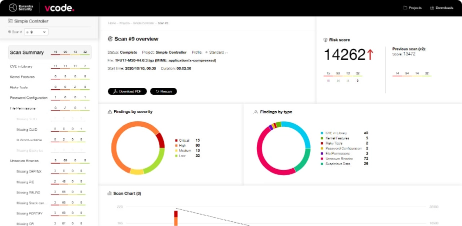
Supply-chain Security and SBOM
Karamba’s VCode software seamlessly analyzes the device firmware, automatically creates a software bill of materials (SBOM), identifies vulnerabilities, and advises on how to remediate them.

Mitigate.
Vulnerabilities and Security Risks to Meet Customer and Auditor Requirements
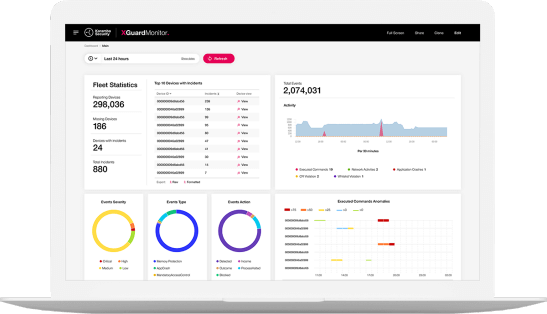
XGuard Suite
Onboard Security
Secure boot, software HSM, secure storage, cryptographic libraries
Allow List
Assure runtime integrity against malware attacks
Access Control
File protection against altering or removal of sensitive files
Host IDPS
Monitoring 15 indicators that signal cyber-attacks in the making

Comply.
Meet industry regulations with no R&D interference
Meet Regulations
Karamba’s portfolio enables device manufacturers and OEMs to meet industry regulations, such as ISO/SAE 21434, FDA (Section 524B in FD&C Act), EU MDR, and EU CRA without affecting product time to market. The portfolio’s holistic coverage is tailored to the most rigid industry security regulations.

Vulnerability Management
VCode Vulnerability Management offers continual security by assembling new vulnerability data from multiple sources, prioritizing them by blast radius, and advising on how to mitigate them.
Continuous Hardening
Integrated into customers’ CI/CD pipelines or software build servers, Karamba’s products continuously monitor the security posture of each firmware version, and add security controls to the firmware, making it ready for release and for meeting auditor and customer requirements.
Want to Learn More?
Israel
24 HaNagar Street
Hod Hasharon
45277-13
Tel: +972 9 88 66 113
USA
41000 Woodward Ave
Building East, Suite 350
Bloomfield Hills, MI 48304
Tel: +1 833 4KARAMBA