Securing IoT Devices
Guarding the IoT from attackers
What Is The Problem?
IoT merges the physical and IT worlds. Connected medical devices, printers, surveillance cameras, and smart factories, have no well-defined perimeter. Cloud, mobile and world-wide-web connectivity are punching holes in perimeter security, and enable hackers to gain access to those connected devices, jeopardizing data privacy and customer safety.
Product security standards such as NISTIR 8259, UL2900, US Executive Order 14028, and FDA endpoint directives require product manufacturers to protect their devices against cyberattacks, and assure supply-chain security. Applying those cybersecurity requirements have a significant toll on R&D processes -- hence time-to-market and revenue loss impact -- as well as on the device architecture.
Trusted by
How Karamba Secures IoT Devices
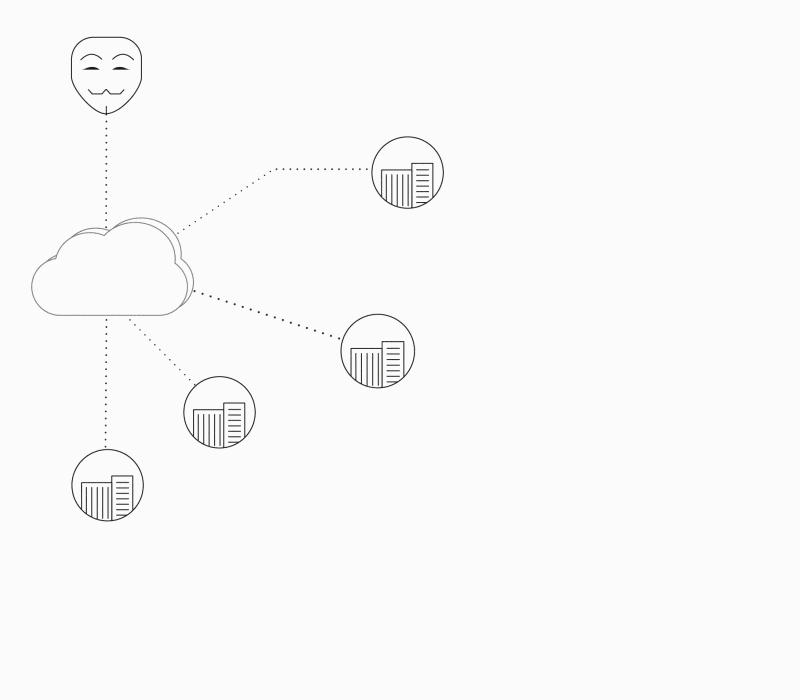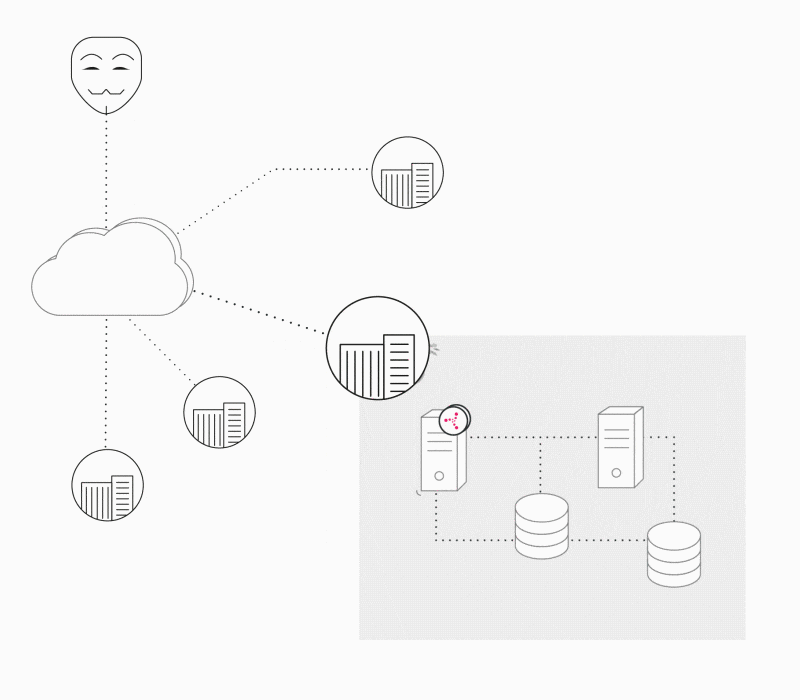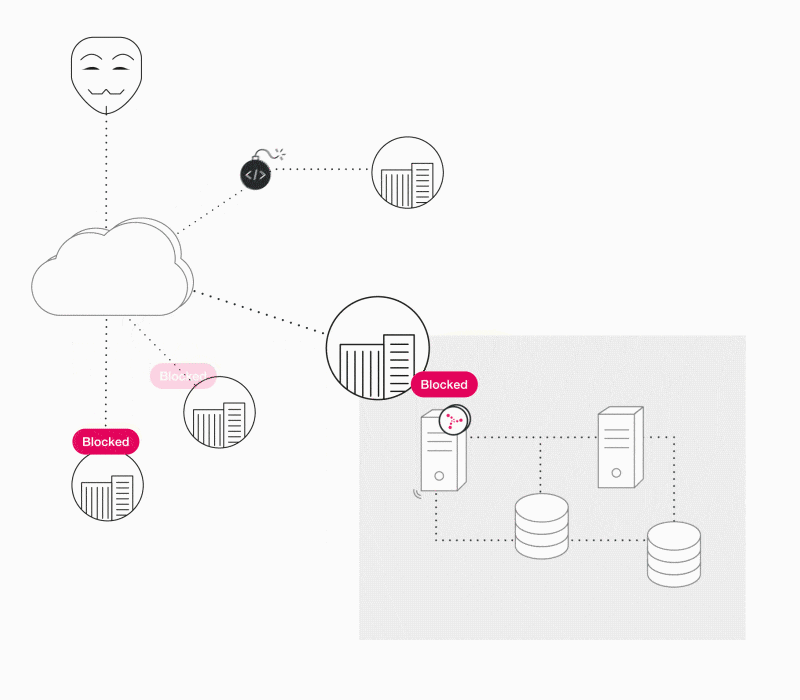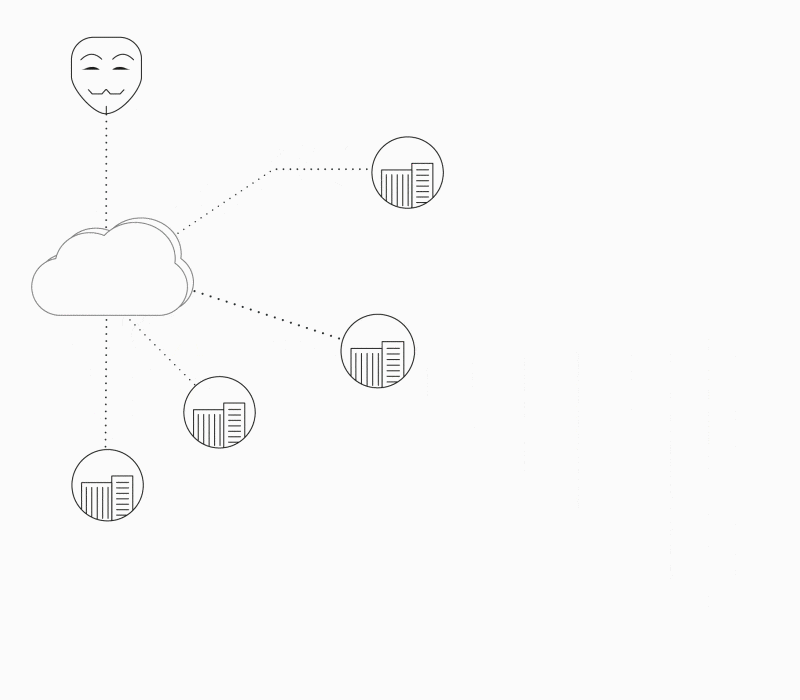
Automatically building security into the connected system is the foundation of Karamba Runtime Integrity technology for the automotive world. Addressing the broad IoT market, the XGuard suite provides unparalleled self-protection against device control loss. Buffer overflows can result in foreign malicious code or code-reuse attacks (such as return-oriented programming) which can be self-detected and self-blocked with Karamba XGuard.
After the attack is detected and blocked, XGuard provides a detailed report of the attack to the device manufacturer.
Automatically embedding cybersecurity into endpoints has always been a sought-after goal, but it has been hindered by performance restrictions. Karamba’s solution allows manufacturers to automatically apply this technology to seal systems during production. Furthermore, Karamba’s solution has proven to have negligible performance impacts in the resource constrained in-vehicle environment.
Deterministic Security
Self-protection is a new paradigm in Security by Design, which aims to detect and prevent attacks in runtime. The factory settings of security policies are defined in the software build process, including the “known good” which the system needs to adhere to.
Any modification from the product’s automatically built security policy is detected as a violation that can be blocked by the device itself and reported for further investigation or other configurable auto-behavior.
Edge Devices
Zero-Day and Day-One attack prevention. The concept of sealing the device according to its known good enables the connected device to protect itself from cyberattacks.
Deviations from the device's known goods must not be allowed. They are deterministically detected and prevented. This approach enables users to detect and prevent new attacks and does not require security updates.
Benefits
Learn more about our Products & Services for IoT

XGuard Secure Boot for Containers
Learn more about how container images can be authenticated before each instantiation.

XGuard for IoT Device Security
Read about the products of XGuard Suite and how they protect IoT devices.
VCode for IoT Product Security
Aligned to Agile SDLC, VCode helps manufacturers validate their code continuously.
Contact us to discuss IoT Product Security
Israel
24 HaNagar Street
Hod Hasharon
45277-13
Tel: +972 9 88 66 113
USA
41000 Woodward Ave
Building East, Suite 350
Bloomfield Hills, MI 48304
Tel: +1 833 4KARAMBA











