Blog
Act now on software integrity in Critical Infrastructure
Tal Ben-David | August 8, 2022

Recently, HP announced implementing Karamba Security’s XGuard CFI into its business printers in order to protect against zero-day vulnerabilities. This new layer, embedded into the most secure printer in the world, provides protection against Return-oriented programming (ROP) attacks. In the extremely exposed world of connected office printers, this security control decision is a very reasonable one.
Tractor – IN, Scooter – OUT: The legislation mandating automakers to protect against hackers has hit the road
Udi Etsion, for Calcalist | January 14, 2022

By Udi Etsion. Originally published on Calcalist, January 14, 2021
Starting in July, protection against cyber attacks will be mandated for all new vehicles in Europe. The head of the UN group that led the legislation clarifies why it is important to protect even a tractor – but not a scooter. Israeli cybersecurity companies are inundated with inquiries from manufacturers.
Software Composition Analysis vs. Binary Analysis - What are the differences?
Assaf Harel | July 29, 2021

While one started as a way to map open-source components for license compliance purposes, the other started as a penetration tester’s tool, helping white-hat hackers analyze binary files of embedded systems.
Why We Offer Software Bill of Materials (SBOM) Generation and Alerts for Free
Karamba Security | July 21, 2021

Following the increase of supply chain attacks, Karamba has recently launched a free Software Bill of Materials (SBOM) analysis and free relevant CVE alerts tool. In this blog post we will explain why it is the right time to manage an SBOM and stay on top of new vulnerabilities.
The Darknet – A Haven for Criminals Under Your Nose
Nir Yehoshua, Security Researcher | May 30, 2021

The anonymity of the Darknet has attracted criminals, including cybercriminals and threat actors who offer attack services, research and development of vulnerabilities of websites and recently - more and more IoT devices.
GitPaste-12 Swiss-Army-Knife Malware Compromises IoT Devices Using 12 Common Vulnerabilities
Karamba Security | November 11, 2020

The worm uses GitHub and Pastebin to download its malicious code (Dropper) – hence its name. GitHub and Pastebin are two well-known websites that usually are not blocked by enterprises, and their connections are encrypted.
How Vehicles Right to Repair will Expose Massachusetts Residents to Cyberattacks
Assaf Harel | September 29, 2020
.jpg)
The initiative passed with overwhelming voter support on November 6, 2012, with 86% for and 14% against. Motivation was clear: to enable vehicle owners to repair their cars and light trucks anywhere they’d like, hence reduce repair costs.
How Lack of Product Security Caused Zoom Customers’ Defection
Assaf Harel | May 12, 2020

In the past two months, Zoom’s users experienced multiple cybersecurity breaches due to Zoom’s lack of product security. Those breaches enabled hackers to intervene in online meetings and compromise the security and privacy of Zoom’s users. Therefore, dozens of companies and organizations banned their employees from using Zoom.
Closing 2019 with CES2020 – A Milestone Year for Karamba Security, and Here Comes 2020
Amir Einav, VP Marketing | January 7th, 2020

Like clockwork, CES starts tomorrow and marks the beginning of our annual technology cycle. This is the opportunity to look back at what’s been a big year for Karamba, and imagine what’s coming.
The FBI Agrees – IoT Devices Post Hacking Risks, and Better Cybersecurity Vigilance is Needed
Karamba Security | December 11th, 2019

The FBI statements put the onus on the consumer to secure the device, but these devices often come with default passwords and customers can’t always be relied upon to carry out the over-the-air updates the companies send for their devices.
Survey: Consumer IoT Customers Expect Manufacturers to Embed Security in Devices
Karamba Security | December 8th, 2019

The survey, entitled “Consumer Attitude Towards IoT Security” found that 74% of respondents expected their consumer “Internet of Things” devices to be secured by manufacturers, and as much as 87% believe it is the responsibility of manufacturers to do so.
What is Host IDPS built with Control Flow Integrity (CFI)?
Karamba Security | November 4th, 2019

There is no such thing as a hermetically sealed connected device and attackers are always looking for vulnerabilities in code and ways to exploit them. With host IDPS built with Control Flow Integrity though, vehicle ECUs have a state-of-the-art cybersecurity tool to defend themselves.
For Cybersecurity, it’s That Time of the Year Again
Assaf Harel, Karamba Security Chief Scientist | October 6th, 2019

The “hacking season” follows DEFCON and BlackHat each Summer, as hackers work to exploit newly-disclosed vulnerabilities before customers can install patches. This cycle gives hackers a clear advantage and it’s time for a paradigm shift.
Why Control Flow Integrity is More Important Than Ever
Assaf Harel, Karamba Security Chief Scientist | September 26th, 2019

With billions of resource-limited, connected vehicles and devices set to hit the market in the coming years, there is a clear and present need for CFI that can be seamlessly embedded into these devices without performance drag, false positives, or delays in go to market.
Marquee BlackHat Presentation Shows the Need for Control Flow Integrity in Automotive Cybersecurity
Karamba Security | September 10th, 2019

It is no longer sufficient to have reactive cybersecurity tools. With CFI, manufacturers have the most effective and state-of-the-art runtime threat detection tool at their disposal to ensure that connected machines adhere solely to their factory settings.
A Fish out of Water at DEFCON: What Made the Car Hacking Village a Good Time, and My Takeaways about the Challenges of Securing Connected Devices
Adili Shimoni | August 27th, 2019

Earlier this month in Las Vegas, Karamba’s Adili Shimoni had a classic fish out of water experience at DEFCON. In this post, she looks back on an eye-opening week in Vegas, and her takeaways about what it all means for the world of connected devices.
URGENT/11 Vulnerabilities in VxWorks Show the Difference between IT and OT - And When They Come Together as IoT
Karamba Security | August 8th, 2019

Of the 11 zero-day vulnerabilities found by Armis, six “are critical and enable Remote Code Execution (RCE).” In this post, we examine how this discovery indicates the importance of embedded security.
“There Must Be No False Positives”
Karamba Security | July 29th, 2019

Last month, Karamba Security’s Director of PMO, Helen Buchumensky spoke at the German Association of the Automotive Industry (VDA) conference about the importance of cybersecurity in safety critical systems, and why it is crucial that it doesn’t clash with Automotive functional safety requirements. This post is based on her presentation.
Cyber Warfare in the Middle East Highlights the Need For Deterministic Cybersecurity
Amir Einav | July 28th, 2019

Recent cyberattacks launched by the US and other militaries are a reminder of the vulnerabilities that all connected systems have, no matter how sophisticated or highly-classified they are.
The Writing is on the Wall: Product Security Must be Built in by Manufacturers
Ami Dotan, Karamba Security CEO and Co-Founder | July 8th, 2019

A series of recent publications in the US and Europe indicate that the industry - and government - are starting to take note, and realize the importance of embedded security for connected products.
Small Country, Big (Smart Mobility) Dreams
Karamba Security | June 13th, 2019

There’s an elite class of world cities that stand apart from the rest. Cities like Tokyo, Shanghai, London, New York, and San Francisco, which drive the global economy and chart the course of human progress. There are also cities like Tel Aviv that punch above their weight when it comes to innovation, talent, and the ability and desire to shake things up a bit.
Intel Shadow Stack – A Bridge Too Far for the Tech Giant?
Karamba Security | June 11th, 2019

Intel has yet to deploy its Control-Flow Enforcement Technology (CET) in its for-market processors, yet another testament to the importance of control flow integrity (CFI) for addressing in-memory cyberattacks.
In Baltimore Cyberattack, the Blueprint for Ransomware Mayhem
Karamba Security | May 27, 2019

Imagine your data and the keys to your operating system have been seized in the hands of faceless, nameless hackers who caught you slipping. They’ve named their price and the clock is ticking – pay up or lose all access to your system.
Karamba, Check Point, and Mobileye to Represent Israeli Industry in First-Ever Israel-Taiwan High-Tech Forum
Amir Einav, VP Marketing | August 24, 2018

Karamba Security, Mobileye (INTC), and Check Point Software (CHKP) were selected as the three companies invited to present the Israeli high-tech industry in a business-to-businees forum held by the Taiwan External Trade Development Council (TAITRA) this week.
Karamba Security's Challenge of RiCAN Morty at DEFCON's Car Hacking Village
Roi Inbar, Innovation Engineer | August 16, 2018

DEFCON is one of the biggest Hacker conferences – a blend of curious, creative, geeks and professionals come to one place with the aim of looking at the things we use every day in a different way and making them act differently than they were designed for.
At CES, Preventing Cyber Attacks Drove OEM & Tier-1 Interest in Karamba’s Autonomous Security
David Barzilai, Chairman & Co-Founder | January 22, 2018

Karamba Security Suite, CES 2018, Las Vegas, NV.
CES started as a B2C tradeshow and B2B is now equally important. For the automotive industry, cybersecurity was one of the major areas of interest among OEMs and Tier-1s who came to Las Vegas to learn about attack vectors and prevention.
Extracting the Content of a QNX IFS Image
Evgeny Dratva | October 19, 2017
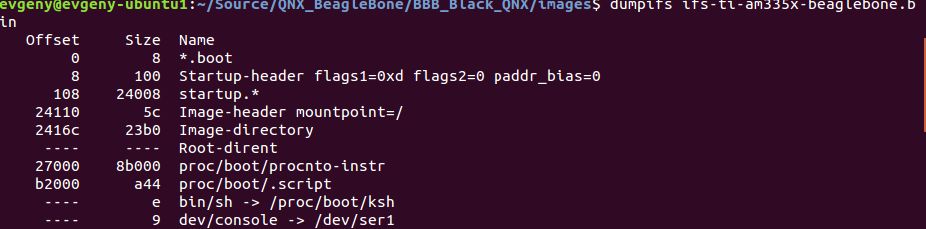
How to approach dumping a QNX Image
While integrating Karamba protection into a QNX IFS image, I found that I first needed to extract the contents of a ready IFS image in order to inspect the binaries on the build machine for Karamba whitelisting purposes. I needed to know what those binaries would look like in their “final” form, after they’ve been stripped of debug symbols and otherwise modified by the IFS building utility.
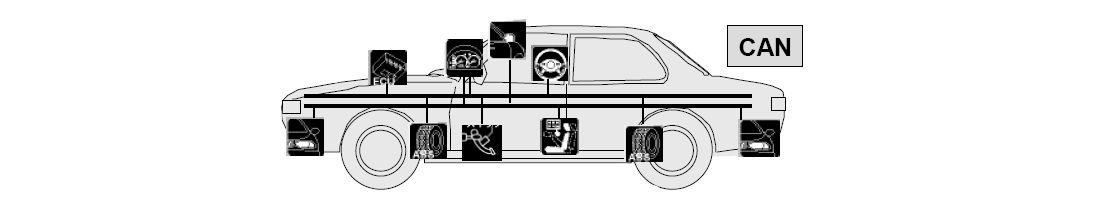
Changing CAN Protocol isn’t a Solution – ECU Hardening Is
David Barzilai, Chairman and Co-Founder | September 12, 2017

CAN Protocol Vulnerability
Recently, Trend Micro published a technical brief discussing a vulnerability they found in the CAN protocol, which enabled denial of service (DoS) attacks to be invisible to CAN-based intrusion detection solutions. In the technical brief, they recommended that car manufacturers change CAN protocol in their vehicle, in order to make cars immune to such DoS attacks.
The Connected Car Security Seminar Tokyo, Japan
Karamba Security | July 16, 2017

Asgent, Inc., Sumimoto’s SCSK Corporation, and Karamba Security hosted the Connected Car Security Seminar on Autonomous Security Products in Tokyo, Japan on July 3rd, 2017. The Seminar featured methodologies behind security protection of Autonomous Vehicles focused on Electronic Control Units (ECUs).
What Happens When Car Scrapping Goes Wrong?
Karamba Security | July 13, 2017

While it’s nice to think that all cars go to Car Heaven, in reality they go through a scrap metal recycling process. In order to recycle the remains of your vehicle, you need to get a special permit and find an Authorized Treatment Facility (ATF).
Karamba Steps up to Cross-industry Calls on Autonomous Car Security
David Barzilai, Chairman & Co-Founder | June 08, 2017

Implementations to Automotive Connectivity
Connected cars increasingly rely on computer processors and upwards of 100 million lines of computer code to operate. With the proliferation of processors and vehicle software the cyberattack surface and sophistication of hacks has grown.
Introducing a Different Cybersecurity Solution - EcoMotion
Karamba Security | May 18, 2017

EcoMotion 2017
EcoMotion is a community with over 700 affiliated organizations related to the Smart Transportation sector. EcoMotion’s 2017 Main Event presented a showcase of vehicle technology companies and a variety of panels and presentations. Ami Dotan, CEO & Co-Founder of Karamba Security, was invited to participate at the “Cyber for Cars” panel to answer paramount questions that concern the automotive cyber security industry.
A Different Auto Cyber Security
Assaf Harel, CTO & Co-Founder | May 16, 2017

Security bugs in the connected vehicle
In A hacker’s guide to fixing automotive cybersecurity, Charlie Miller puts in perspective which cyber security challenges exist for the automotive industry. The article’s conclusion is that all software -even the most reliable- contains security bugs. Even the ones coming from software mammoths such as Microsoft, Google and Apple. The ramifications of these vulnerabilities in cars, evidently, can be severe.
Want to learn more?
Contact UsIsrael
24 HaNagar Street
Hod Hasharon
45277-13
Tel: +972 9 88 66 113
USA
41000 Woodward Ave
Building East, Suite 350
Bloomfield Hills, MI 48304
Tel: +1 833 4KARAMBA