Karamba VCode
Binary Analysis for Supply Chain Security
Used during software validation, VCode helps automotive OEMs and IoT device manufacturers to automatically identify supply-chain cybersecurity issues and address them before production.
VCode software identifies, prioritizes, and mitigates security gaps in the software image, specifically third-party modules.
Provides visibility to Product Security Posture and Risks
- Highlights developers’ security oversights
- Automatically finds data oversights
- Serves as a product security scorecard for internal viewers and for customers
Suggests remediations, with context and priorities
- Platform-specific instructions
- Possibility for managed services to shorten remediation time
Generates reports and compliance validation summaries
- Management report on security level and progress
- Security validation to demonstrate to customer
- Security findings mapped to industry standards
- Simplified compliance validation via checklists
Can be integrated into the Continuous Integration/ Continuous Design (CI/CD) pipeline, or used to scan image binaries manually, with a simple drag & drop action
- Command Line Interface to process findings data: pipe the detailed structured output (types and locations of oversights) to mitigation processes
- Simple integration with CI/CD systems, to trigger action items specific to the type of finding
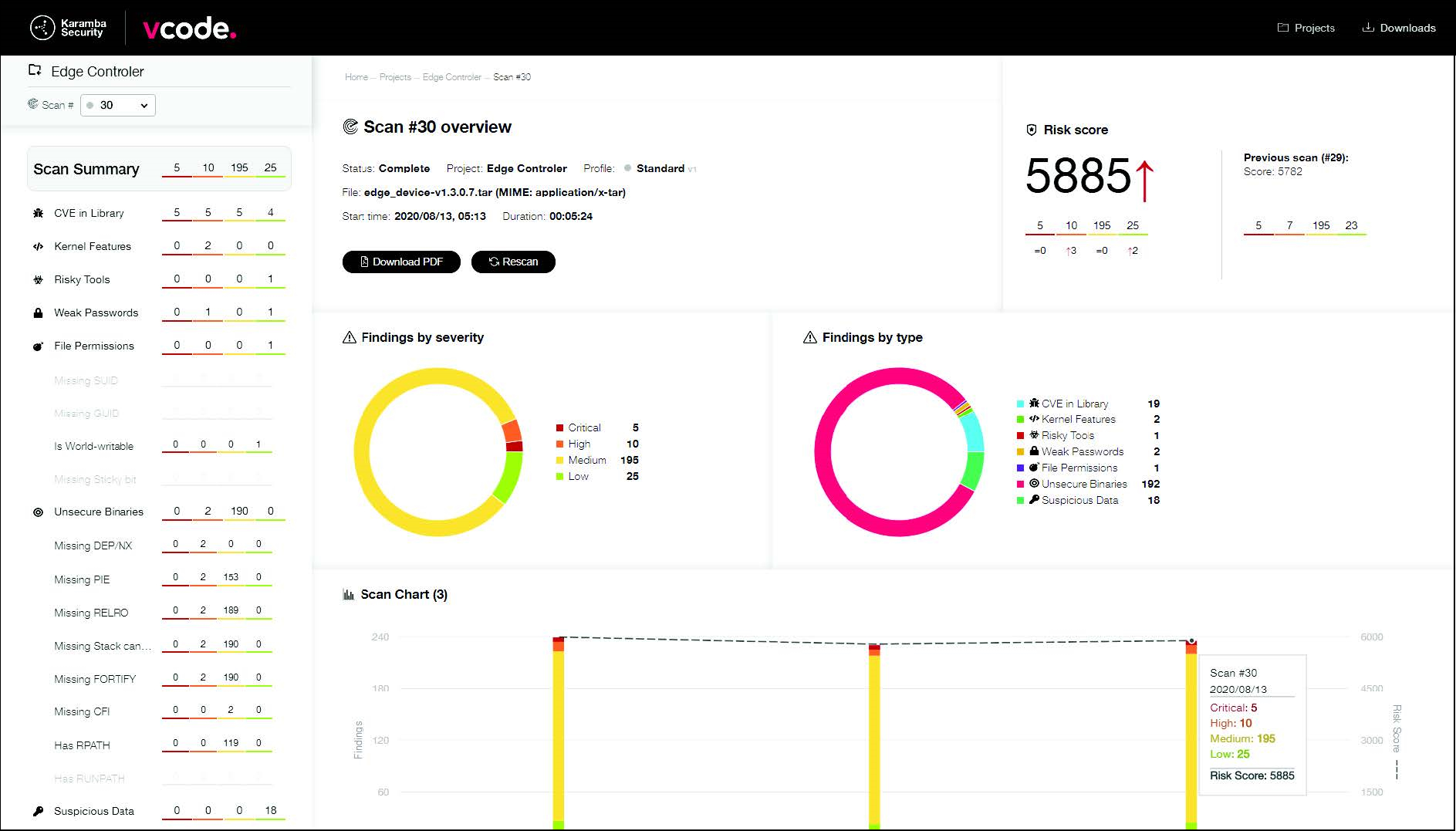
Analysis Findings
Weak Passwords
- Strong passwords are an important first line of defense for connected systems that include remote access, both automated and manual. VCode’s scanner analyzes common password definitions and identifies security gaps.
Kernel Features
- This scan points to kernel configuration options that aid in preventing certain types of cyber attacks or make them much harder. You can use these options to create a more secure system, reducing the attack surface for the OS kernel.
CVE In Library
- Common Vulnerabilities and Exposures are publicly disclosed security flaws found in the software libraries and applications on your firmware image. This scanner searches for the use of vulnerable versions of common and popular libraries. Fileless, in-memory attacks are based on vulnerabilities that enable attackers to map and manipulate the runtime execution of binaries.
Unsecure Binaries
- Various compiler, linker and OS security features are available during the build, which add runtime checks and protection mechanisms that reduce in-memory attack surfaces. This scanner highlights risky configurations of some or all of these features.
File Permissions
- The Linux operating system has a permission model that distinguishes file permissions for users and groups. Files that are configured with less restrictive permissions may be modified or abused by attackers to run with higher privileges (e.g., as ‘root’), and to modify system configuration. The scanner identifies files that are configured with less than recommended restrictive flags. For example, it pinpoints applications that do not have the SUID flag, which would block an attacker from running them with higher privileges.
Software Bill of Materials (SBOM)
An essential part of VCode is the SBOM – required for compliance with cybersecurity standards such as UN R155. This tool provides details on the filesystem(s) and on each component in the image, including third-party software: location, CVE count, highest severity for CVEs, dependencies, and (where available) library version number and associated license type. An easy-to-use filtering mechanism allows for studying the data and identifying actionable insights.
Supported Formats
- VCode can scan
- Software images provided by build systems such as Yocto
- Firmware images ready to be flashed onto a specific device (including ova/vmdk images and MBR disk images)
- Linux kernel configurations
- Single files (executable, library, jar, apk)
- Supported filesystems include cpio, ext4, jffs2, squashfs, and vfat.
- Archive file support includes bz2, gz, tar, xz, and zip, including nested initrd/initramfs.
- OS support: Linux, Android (sparse, payload.bin, super.img, boot.img), QNX, FreeRTOS and AUTOSAR.
VCode’s Security Advantages
Read About Our Security Solutions
VCode for Automotive
Aligned to Agile SDLC, VCode helps OEMs validate their code continuously.

VCode for IoT Product Security
Aligned to Agile SDLC, VCode helps device manufacturers validate their code continuously.

VCode Supported Formats
Use VCode to scan a wide range of file and archive types for vulnerabilities and configuration issues.
Contact us to discuss VCode and SBOM!
Israel
24 HaNagar Street
Hod Hasharon
45277-13
Tel: +972 9 88 66 113
USA
41000 Woodward Ave
Building East, Suite 350
Bloomfield Hills, MI 48304
Tel: +1 833 4KARAMBA
Germany
Wasserburger
Landstr. 264, Munich
81827
Tel: +49 892 1547 7583


