Embedded Application Whitelisting
Automatically built, prevents loading of unauthorized executables
Karamba XGuard Whitelisting:
Deterministically Prevents The Loading
Of Unsigned Executables
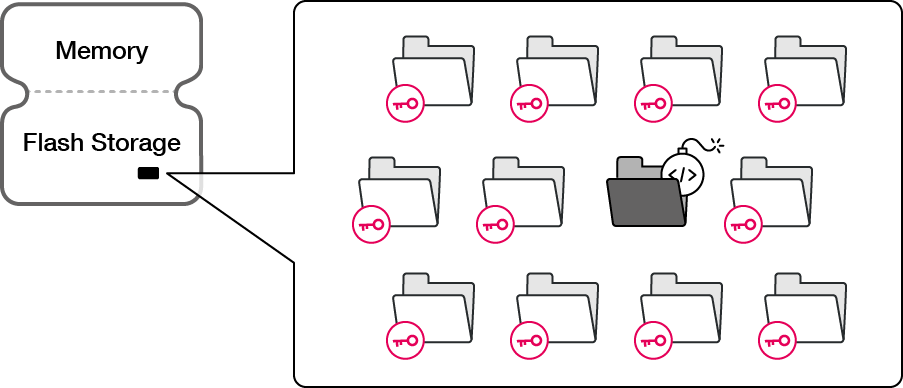
Application whitelisting is not a new idea in security, and in a confined application the “known good” list is a very effective security measure against dropper attacks.
Hackers looking to upload new scripts, binaries or libraries into memory during runtime will be blocked, as the whitelisting compares each executable with the contents of the authorized list.
Karamba's secret sauce is the automatic process to map and build this whitelist. In very large applications with thousands of executables, only an automatic and granular building of the whitelist is practical to protect the code.
Given the dynamic nature of the supply chain, Karamba XGuard Whitelisting has a built-in mechanism to allow external signed binaries from third-party suppliers as well as update diffs from the image authority.
XGuard Whitelisting Advantages
See Why Our Security Solutions Win Awards

XGuard for Automotive
Read about the products of XGuard Suite and how they protect automotive systems and devices.

XGuard for IoT Device Security
Read about the products of XGuard Suite and how they protect IoT devices.

XGuard Bolt-On Security for IoT
XGuard controls can be added on after the build.
Want to learn more?
Contact UsIsrael
24 HaNagar Street
Hod Hasharon
45277-13
Tel: +972 9 88 66 113
USA
41000 Woodward Ave
Building East, Suite 350
Bloomfield Hills, MI 48304
Tel: +1 833 4KARAMBA


