Overview
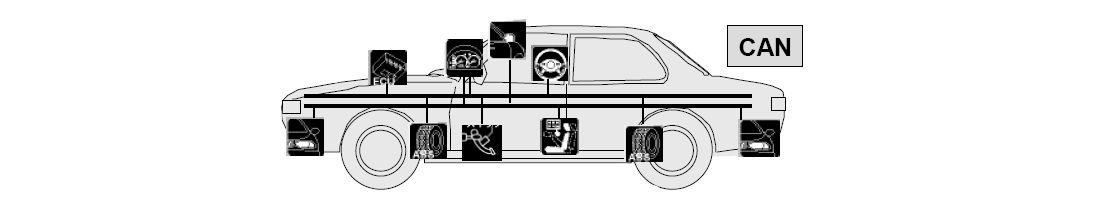
CAN Bus - Controller Area Network bus - is a high-integrity serial bus system for networking intelligent devices adopted by the automotive industry and, in 1993, it became the international standard known as ISO 11898.
A modern vehicle may have as many as 70 electronic control units (ECUs) for various subsystems connected to each other via CAN Bus to govern almost every function — from engine timing and traction control to side-mirror adjustment.
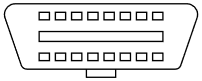
Accessing the car’s CAN Bus is possible using the OBD II Port. OBD is an acronym for “on-board diagnostics” and refers to vehicle’s self-diagnostics and reporting capability. Initially it was intended to help mechanics run quick vehicle diagnostics. The early versions of it allow checking for possible problems with the engine. Nowadays, in addition to the diagnostic interface, it includes access to the vehicle CAN Bus. Almost every vehicle sold from 1996 until present should have an On-Board Diagnostics (OBD-II) Port. Use the following link to locate your car’s OBD-II Port.
Building the Sniffer
After considering various options for a CAN controller + computer, we decided to go with the PiCAN2
board to provide CAN-Bus capability for the Raspberry Pi. The RPI 3 is more convenient than the
Arduino because of its Linux shell and access to apt-get with can-utils packages. Also, the
PiCAN2 is an affordable shield, and this makes the combination with RPI 3 a perfect and affordable
hardware choice. It uses the Microchip MCP2515 CAN controller with MCP2551 CAN transceiver.
Connections are made via 3-way screw terminal as follows: CAN_H -> OBD II pin 6,
CAN_L -> OBD II pin 14; using a lighter USB adapter as a power source for the RPI.
Utilizing the PICAN is done through an easy-to-install SocketCAN driver. As a starting point the best is to start with a brand-new Raspbian image. Download the latest version
After first-time boot up, do an update and upgrade first:
# sudo apt-get update
# sudo apt-get upgrade
# sudo apt-get install can-utilsTo enable the SPI bus and load the kernel module, add the following lines to the /boot/config.txt:
dtparam=spi=on
dtoverlay=mcp2515-can0-overlay,oscillator=16000000,interrupt=25
dtoverlay=spi-bcm2835-overlayReboot and run ifconfig to see if the can0 exists:
# sudo ip link set can0 up type can bitrate 100000Running the candump util:
# candump can0
(1512998188.915501) can0 156#F5C200000721
(1512998188.916749) can0 18E#080045
(1512998188.920957) can0 091#8023C8020000001A
(1512998188.923367) can0 13C#00C400D500000402
(1512998188.923607) can0 158#0000058700000006
(1512998188.923853) can0 17C#000006300000000B
(1512998188.924062) can0 188#000000010033
(1512998188.924228) can0 1DC#02063021
(1512998188.924376) can0 1ED#01FF2B
(1512998188.925487) can0 156#F5C200000730
(1512998188.925726) can0 1A6#000CC0367C8000A1
(1512998188.926747) can0 18E#080054
(1512998188.930961) can0 091#8023C80600000025
(1512998188.931203) can0 1A4#006600000000001C
(1512998188.931446) can0 1AA#7FFF000000006612Running candump with the -f option will redirect the output into a log file.
Analyzing the Data
After we have sniffed the CAN bus, a scripting language (for example, python) could be used to analyze the data: detect patterns, detect connections between things the car does and examine the CAN bus traffic that it generates.
See below an example of using python to convert the candump file into CSV.
import csv, argparse
parser = argparse.ArgumentParser(description='CANDUMP to CSV converter - Karamba Security')
parser.add_argument('-f', action="store", dest="fileName", help="input file CSV, format: (time), can interface, msgid, data")
results = parser.parse_args()
f = open(results.fileName, 'r')
reader = csv.reader(f, delimiter=' ')
print ('time, intrface, msg id, data')
for line in reader:
time = line[0]
intr = line[1]
msgid, data = line[2].split('#')
print (time.strip(), ',', intr.strip(), ',', msgid.strip(), ',', data.strip())Learn more about Automotive Security Systems
Following the increase of supply chain attacks, Karamba has recently started to provide free analysis of software binaries, to list in-use open-source libraries, and also suggest free CVEs monitoring.