Why SBOM libraries are so important in the SDV age, and how to assess the risks and mitigate them according to the ISO/SAE 21434 standard.
What is an SBOM?
Simply put, it’s the full list of ingredients that are compiled within a specific product. To developers, it’s a ‘Software Bill of Materials’: A formal, machine-readable inventory of software components, dependencies, and their hierarchical relationships. Software vendors often create products by assembling many open-source and commercial components. When dealing with an advance and complex piece of software it is often extremely hard to evaluate what the integrated components are that comprise the complete product.
SBOM is the tool that can help organizations to avoid integrating harmful or defective software components, or software that contains known or unknown vulnerabilities. Manufacturers use the SBOM to track different pieces of software and to make it easy to locate problems. SBOMs also include attributes that can identify individual components in a standard data format. The most common SBOM formats are SPDX, CycloneDX, and SWID.
What are the benefits of an SBOM?
The benefits of understanding SBOM inventories is in reduction of costs, reduction of security risks, and compliance risks. The SBOM assists developers manage dependencies and identify security issues. When a 3rd-party inventory has CVEs (Common Vulnerability Exposures), an SBOM can identify the harmful code and its location. As software and applications created by 3rd-party open-source libraries gain a larger portion of the automotive industry, it is becoming extremely challenging to pinpoint harmful and faulty code. The use of SBOM identification assists in improving software development, in supply-chain management, in vulnerability management, and in high-assurance processes.
- The main benefits include Identifying and avoiding known CVEs
- Identifying security and license compliance standards
- Assessing and quantifying risks in a software package
- Managing mitigations
- Lower operating costs
SBOM in the Automotive industry
In the age of EVs and SDVs, automotive manufacturers commonly purchase software packages and products from 3rd-party suppliers, Tier-1s and subcontractors worldwide. Managing all these packages of various software and different operating systems is extremely critical. This is where the SBOM comes in. The SBOM tells manufacturers where each library comes from, and details every software component that makes a vehicle run. A scan of these libraries will reveal the entire infrastructure, and will help prioritize remediations.

How does SBOM aid in preventing and mitigating cyberattacks?
When generating an SBOM, automotive manufacturers and Tier-1 suppliers can discover vulnerabilities and flaws in software components, and quickly identify the affected component. Manufacturers can assess the usage of this component and understand the introduced risks. Identifying and locating vulnerabilities allows suppliers to mitigate and to produce OTA patches, and allows consumers to apply mitigations independently.

Karamba Security has recognized the potential benefits of a comprehensive SBOM listing, and has perfected a product that can scan and generate an SBOM from any image in operating systems and software languages used in the automotive industry, including AUTOSAR. Karamba’s VCode identifies cybersecurity issues and vulnerabilities in suppliers’ binaries and analyzes misconfigurations, authentication glitches and risky tools that are listed in the Software Bill of Materials. VCode can generate or import an SBOM into its system, connecting to existing CI/CD pipelines without requiring cumbersome analysis processes for each version. VCode prioritizes vulnerability issues according to the ISO/SAE 21434 standard and the UN R155 regulation to expedite FOTA demands. It provides OEMs with complete visibility of SBOM components, including 3rd-party libraries, and can export or import them in CycloneDX and SDPX formats.
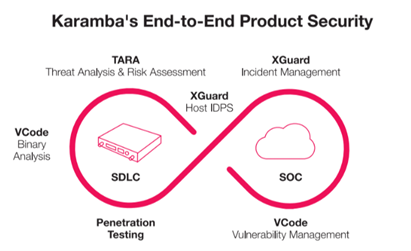
VCode is just one of the various tools and services in Karamba’s End-to-End cybersecurity portfolio.