Implementing CSMS as per the ISO/SAE 21434 standard and the UN R155 regulation.
In recent years, the automotive industry has undergone a massive transformation with the adoption of the ISO/SAE 21434 standard and the UN R155 regulation. These require of OEMs and Tier-1 Suppliers to streamline their EVs and SDVs to comply with directives and to enforce consistent processes and work products creating an ideal CSMS. The goal is to increase cybersecurity for vehicles over their entire life cycle.
What is a CSMS?
This is a method commonly used in the automotive industry to provide engineers with a structured framework that ensures cybersecurity for their vehicles. The implementation of the ISO 21434 standard defines the items involved and identifies risks in the concept phase, and defines verification and validation in the development phase. Identifying these risks is also a requirement of the UN R155 and UN R156 regulations. Traditionally, the CSMS process generates work products that follow the V-shaped development structure; However, as the nature of cybersecurity activity is fast and agile, so too must the CSMS process reflect the speed in which software is updated and patched, by applying a continuous, infinity-shaped development cycle structure.
When commencing a new cyber-certification and homologation project, organizations should evaluate their suppliers from a cybersecurity perspective, and identify and manage their weaknesses and vulnerabilities. The first step is harnessing all the stakeholders involved to conform to a scope assessment and a road map. This is an important organizational step. It means understanding whether your organization is prepared to fulfill the CSMS process. You might need a dedicated cybersecurity team that is fully committed. Usually, an overview work product template will be introduced at this time, encompassing the main issues:
- Listing the work products ahead
- Listing the requirements for all dependencies
- Providing evidence from either IT or CISO
- Identifying missing cyber controls
- Incident response
- TARA
The intention is to provide a vocabulary, objectives, and guidelines for a common understanding throughout the supply chain. This enables the organization to define cybersecurity policies and processes, implement budgets and supporting processes, manage the risks, and foster a cybersecurity culture.
How does the CSMS work?
Creating an effective CSMS and a cybersecurity gap analysis, in line with the ISO/SAE 21434 standard and the UN R155 regulation, should include these essential functions:
- Adopting the CSMS ISO 21434 requirements
- CIRP: Threat escalation protocols
- Cyber risk management policy
- RACI: Matrix charts and assignments
- Suppliers’ security activity
- Maintaining a complete CSMS
Adopting the CSMS ISO 21434 requirements
Sections 5 through 8 of the Standard speak to organizational management of the cybersecurity process, information sharing, culture, and the audit stage. It clarifies dependencies and responsibilities and verifies the supplier’s capabilities and management. This section also ensures the monitoring and evaluation of cybersecurity vulnerabilities.
CIRP: Threat escalation protocols
CIRP, Cyber Incident Response Plan is a comprehensive method for tackling cyber threats and cyberattacks. It outlines the steps that need to be taken to minimize damage, restore services, and prevent future incidents. Some key elements of CIRP include: incident identification, designation of team roles to respond to these threats, evaluation of the severity and impact of these incidents, isolation, and mitigation to prevent further damage. Additionally, the plan addresses gathering of forensic evidence to understand the nature of the attack, notification of all relevant stakeholders, validation of the integrity of the restored systems, and post-incident reviews.
Cyber risk management policy
It is imperative to clearly define the goals of the risk management process and to protect the confidentiality, integrity, and availability of information assets, ensuring compliance and maintaining continuity. This stage includes techniques such as risk scoring, risk matrix, or qualitative/quantitative analysis. It might also establish procedures for identifying and categorizing cyber risks; specifying preventive measures to mitigate risks; and implementing strategic control practices.
RACI: Matrix charts and assignments
This is a framework to clarify and define roles and responsibilities within the project for each of the activities being carried out: Responsibility, Accountability, Consulting, and Information. - It is often represented in the form of a RACI matrix chart, which visually displays the various roles and their level of involvement in various processes.
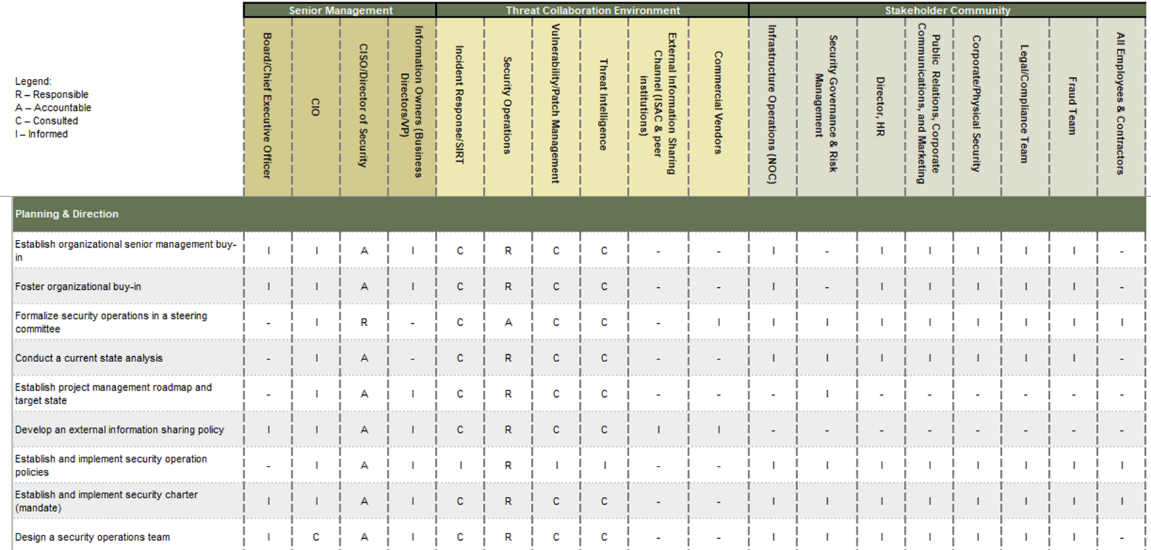 RACI Chart
RACI Chart
Suppliers’ security activitiy
Continued vendor’s cybersecurity awareness: Evaluating your supplier’s cybersecurity capabilities, conforming to standards, and alignment to a Cybersecurity Interface Agreement (CIA). This involves assigning points of contact on both sides, listing activities to be performed, defining milestones and ownership, logistics, and a RASIC table for work products. The RASIC allows you to put the work products into a work plan with milestones.
Maintaining a complete CSMS
This involves continuous re-evaluation: . Learning of new vulnerabilities and threats to update the TARA, and putting into place proper risk mitigations that enable shortening or eliminating the learning phase. Have weekly or bi-weekly meetings, periodic cyber awareness campaigns, and annual cyber steering committee meetings. These discussions are agile and facilitate sharing of any early findings which could provide an opportunity to fix critical processes sooner. The goal is to prevent delays of releases.
Threat Analysis and Risk Assessment (TARA)
- Identify the assets of your product and their cybersecurity properties
- Identify the threats, weaknesses, and exploits
- Assess the damage, and consider the impact
- Calculate the attack feasibility with CVSS, attack potential-based approach, attack vector-based approach, and windows of opportunity.
Once the full scope of the risk is determined, a Risk Scoring matrix is created to help guide you step-by-step to a practical and tailor-made Cybersecurity Goal and Mitigation Concept.
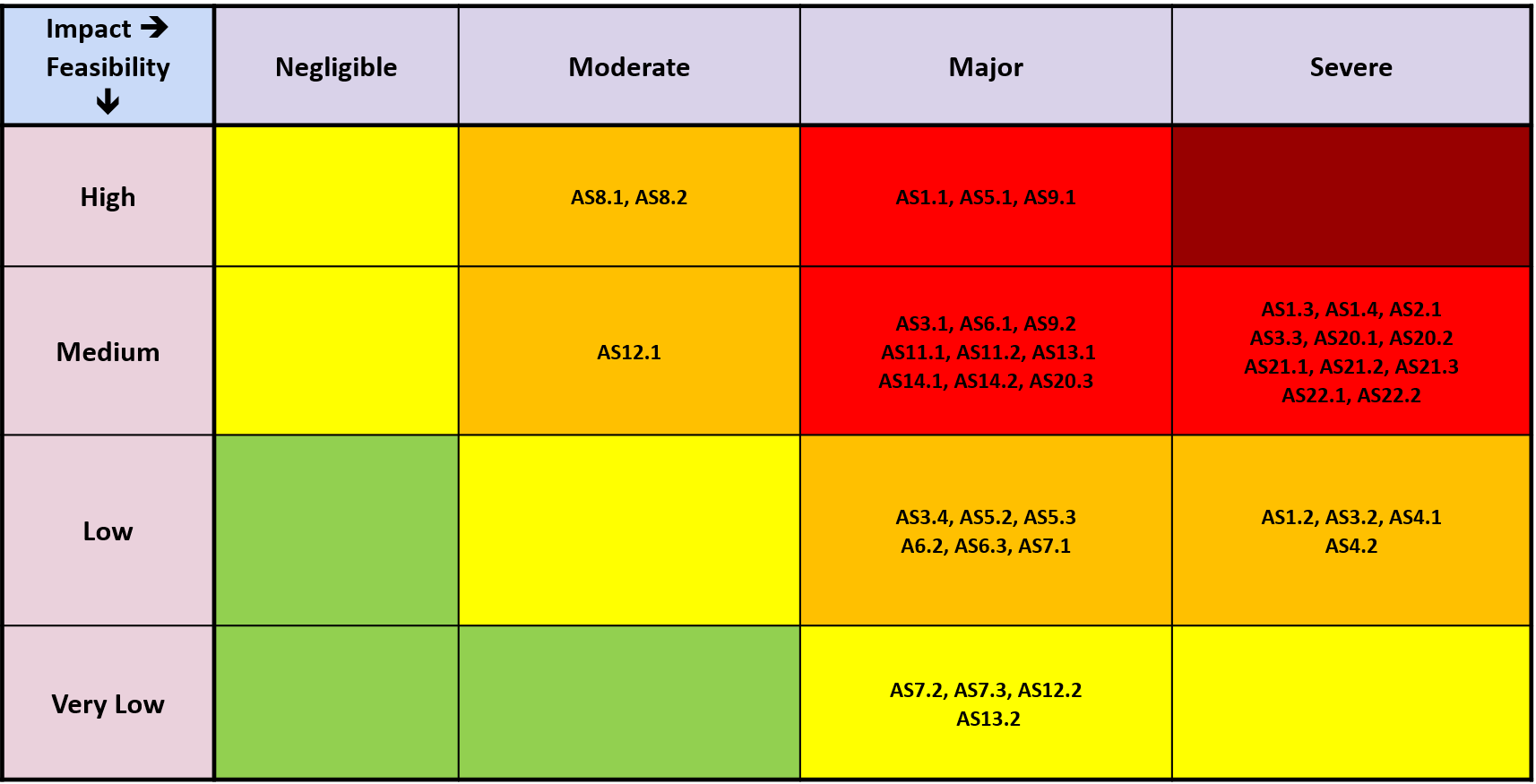 TARA Risk Matrix
TARA Risk Matrix
Additional questions an organization should resolve before creating a gap analysis and while building an ISO standardization kit:
- Does your organization have an information security policy that includes details of resources, processes, and responsibilities?
- When your organization initiates a project, does it take cybersecurity activities into account?
- Does your organization manage and evaluate its suppliers from a cybersecurity perspective?
- Does your organization perform Threat Analysis and Risk Assessments, both generally and from the viewpoint of road users?
- Does your organization implement a process to monitor, evaluate, identify, and manage vulnerabilities?
- Does your organization define cybersecurity requirements and specifications during its architectural design process?
- Before production, does your organization validate that the configurations meet the cybersecurity requirements that were defined?
- Does your organization have an incident response plan?
- Does your organization have a procedure implemented to communicate the end of cybersecurity support for components and enable their decommissioning?
As automotive OEMs and suppliers must meet the ISO 21434 standard and the UN R155 regulation, Karamba Security’s End-to-End Product Security Portfolio accelerates such compliance without delaying the start of production. With a track record of over 100 projects, Karamba’s products and services detect critical vulnerabilities, provide advisories on how to remediate them and how to justify (for homologation purposes) why resolving non-critical issues may be postponed to avoid delays to product release plans.