Why application containers are used, and how they can be secured
Container tools for runtime and orchestration are becoming an integral part of IoT and ECU firmware; in the automotive sector, this is especially prevalent as part of Software Defined Vehicle (SDV) architectures.
Why Use Containers?
Containers usually contain a single feature set of the entire application. This gives IoT device manufacturers much greater agility and updatability of their applications, at lower costs. Containers technology enables manufacturers to deliver software updates for a specific feature set, without needing to re-package and update their entire application.
Container Benefits
The general benefits of utilizing container architectures, applicable for IoT or SaaS applications, include:
- Convenience during development and testing of applications and services
- Environment independence, for portability across platforms
- Simplified deployment of an application to a single command, with no need to install requirements individually
- Facilitated scaling of applications
- Ease of update/upgrade
In particular, benefits for IoT/Automotive systems include:
- Reduced scope and risk: Only applications that are needed are run, free of unused applications that come with a full-blown OS, and segregated within the context of the container.
- No need for repeated flashing of the host OS
- “Diff” updates, reducing needed bandwidth
Risks, and Current Security Solutions Shortcomings
IoT devices and vehicles are exposed to cyberattacks, as any connected system is. If attackers gain write access to the host OS file system, they can easily tamper with any container image because a container image is just a group of folders/files stored on the host machine’s file system.
Existing security solutions for validating container images focus on making sure that the container image pulled from the repository is valid. These solutions are good enough for container applications in Cloud/SaaS environments where the lifespan of the container application is short, as the container image is deleted from the local storage after execution. In IoT and automotive, to save bandwidth costs and to ensure resilience to connectivity loss, the container image is stored on the device for future runs, making it vulnerable to hackers who might infiltrate the device.
There’s a need to validate that they are not tampered with or replaced at the point where a container instance is created out of the image.
Secure Boot protection will not solve this problem. Containers, by their nature, are not an integral part of the device boot sequence, and they can be started/ upgraded/restarted/shut down/ at any point in time. Therefore, conventional Secure Boot validation is not relevant for them.
XGuard Container Authentication
XGuard – Karamba’s IoT security software – offers a strong, automatically created whitelist. Such a security control authenticates images in runtime, making sure that they haven’t been tampered with or hacked. XGuard for Containers automatically calculates the container’s image hash “signature” and creates a policy that contains the hashes of all allowed container images. The policy is stored on the host Linux OS and enforced at runtime when a container instance is created from the image.
Container images can be added/removed/updated without the need to modify the underlying host Linux OS. Karamba XGuard supports these scenarios by allowing the creation of an additional policy that whitelists new/updated container images for the target device.
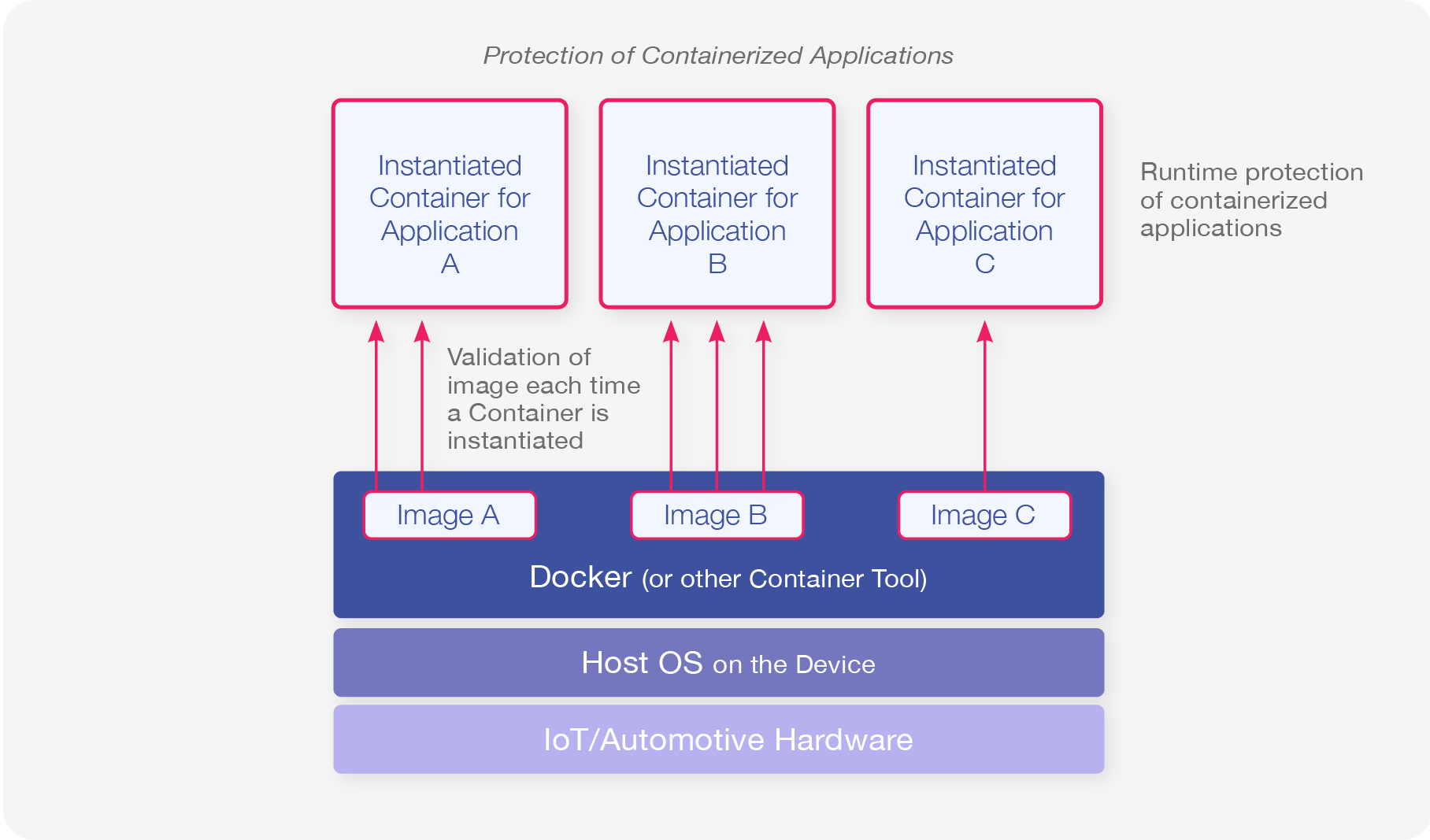
Securing the Running Container
Containers are essentially autonomous execution units; Although they share the kernel with the host Linux OS, they run independently and represent a separate network entity. As such, containers can be targeted by attackers and need to be protected by preventive solutions such as Karamba XGuard.
XGuard’s User-space Only enforcement model is tailored to protect running containers. There are multiple integration points at which Karamba XGuard can be applied:
- Protection at the image build stage, by adding XGuard build steps to the Dockerfile (or similar file for other technologies such as Podman)
- Protection of the container image after the build.
Karamba’s XGuard for Containers provides a full runtime-security feature set for running containers, including: Application Whitelisting, File Protection, Associated Execution and Security Monitoring.
Karamba’s Offerings
At the heart of Karamba’s XGuard suite is its automated host security software, which hardens the automotive ECU or IoT device against malware and in-memory attacks. It ensures deterministic protection and continuous monitoring of the device, with the negligible performance impact of a fraction of a percent to five percent.
In addition to host security and XGuard for Containers, the XGuard suite also includes Onboard Security modules for automotive, SecOC for secure communication, and an event-monitoring system with customizable dashboards. Karamba Security’s End-to-End Portfolio of products and services provides a complete cybersecurity journey that complies with regulatory requirements and connects to the CI/CD pipeline, without the need to recompile or change code or delay product release dates.
To learn more, download the full white paper, XGuard for Container Security, using the Download button below.
