It is no longer sufficient to have reactive cybersecurity tools. With CFI, manufacturers have the most effective and state-of-the-art runtime threat detection tool at their disposal to ensure that connected machines adhere solely to their factory settings.
In a conference hall in Las Vegas, engineers from Tencent Keen Security Labs presented a blueprint for a connected vehicle manufacturer’s nightmare.
In a presentation entitled “0-Days & Mitigations: Roadways to Exploit and Secure Connected BMW Cars,” Keen Lab engineers told the crowd at the BlackHat conference in August how they exploited seven critical vulnerabilities in four separate BMW models through both physical and remote attacks.
Keen Lab’s report details how they found vulnerabilities in the telematics control unit, the infotainment system, and the central gateway. Keen Lab was able to reverse engineer ECU software and mainpulate the connected vehicles’ behavior through arbitrary CAN messages. They reached the ECUs by leveraging a range of attack vectors, including triggering Remote Service via SMS, intercepting in-car HTTP traffic, exploiting the in-car browser, injecting CAN messages onto the K-CAN bus, and by manipulating the “laststatecall” function, among other methods.

To take control of the ECU, the researchers managed to execute code in the target device. As Keen Lab says in the report, “using the Return-Oriented Program (ROP), we could develop a stable exploit to achieve code execution with root privilege in HU-Intel system of NBT (the infotainment system) when navigation map update is triggered via a USB stick.”
Like with other connected devices, the capabilities that allow connected ECUs to provide greater service and convenience to users also open avenues of attack. The report details how BMW’s in-vehicle Next Generation Telematics Protocol (NGTP) allowed the auto maker to provide remote service and trigger commands including locking or unlocking the doors and operating the lights. Keen Lab researchers showed how they were able to manipulate this service and remotely send commands to the vehicles.
Keen Lab referred to their research as “an ethical hacking research project,” and presented their detailed findings in private to BMW three months before they even mentioned them to the wider public. BMW responded with an all-hands-on-deck approach according to Keen Lab, deploying their security team and involving specialists from throughout the company ranks.
Keen Lab’s report also details how all of the attack vectors they found were exploits of remote code execution vulnerabilities, i.e. Keen Lab engineers were able to execute their own code on the device through buffer overflow vulnerabilities that allowed them to hijack the software control flow.
Keen Lab’s state-of-the-art research shows the importance of applying strong security controls in connected ECUs, especially those that are related to safety. A category of solutions designed precisely for that purpose is called Runtime Integrity.
Runtime Integrity products and features include Adaptive AUTOSAR specifications and ETSI IoT requirements, as well as the most effective and state-of-the-art tool of them all - Control Flow Integrity (CFI), which embeds binary validation code in the software to verify that the control flow cannot be hijacked.
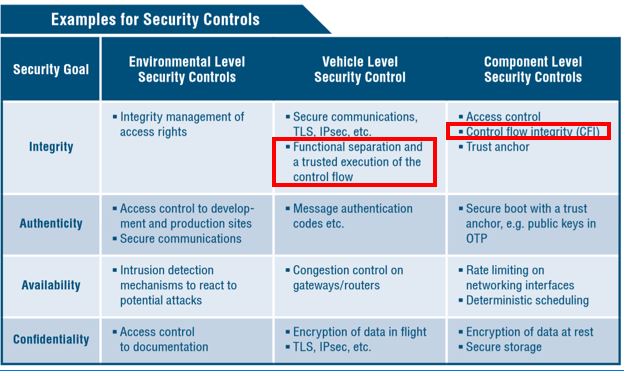
Runtime Integrity, built into the software image, provides the level of self-protection that is required in today’s ECUs. Runtime Integrity ensures that software runs according to a predetermined policy, a known good, and takes decisive action when it detects a deviation from the approved policy. What this means is that even if there is a vulnerability in the software or firmware, CFI can ensure that the device (in this case a vehicle ECU) does not perform any action that was not defined by the manufacturer.
The automotive industry has already taken note. In July, BMW was part of a group of industry leaders – including Audi, Dailer, FCA, and Volkswagen – who published a set of safety and security guidelines for autonomous vehicles. Entitled “Safety First for Automated Driving,” the publication lists CFI as one of the component level security controls that can help safeguard autonomous vehicle cybersecurity.
Keen Lab’s in-depth presentation at BlackHat 2019 was further proof that it is no longer sufficient to have a reactive cybersecurity toolkit that responds to attack attempts, especially considering the vast array of attack vectors and the millions of lines of code in the average connected car. In such a complex landscape, cybersecurity must be built-in and embedded seamlessly into the vehicle before it ever leaves the factory.
In such a complex landscape, cybersecurity must include CFI.
